One of the more recent discoveries resulting from the breach two weeks ago of malware-as-a-service provider Hacking Team is sure to interest Android enthusiasts. To wit, it's the source code to a fully featured malware suite that had the ability to infect devices even when they were running newer versions of the Google-developed mobile operating system.
The leak of the code base for RCSAndroid—short for Remote Control System Android—is a mixed blessing. On the one hand, it provides the blueprints to a sophisticated, real-world surveillance program that can help Google and others better defend the Android platform against malware attacks. On the other, it provides even unskilled hackers with all the raw materials they need to deploy what's arguably one of the world's more advanced Android surveillance suites.
"The RCSAndroid code can be considered one of the most professionally developed and sophisticated Android malware [titles] ever exposed," researchers from security firm Trend Micro wrote in a recently published blog post. "The leak of its code provides cybercriminals with a new weaponized resource for enhancing their surveillance operations."
RCSAndroid includes the ability to:
- Capture screenshots using the “screencap” command and framebuffer direct reading
- Monitor clipboard content
- Collect passwords for Wi-Fi networks and online accounts, including Skype, Facebook, Twitter, Google, WhatsApp, Mail, and LinkedIn
- Record using the microphone
- Collect SMS, MMS, and Gmail messages
- Record location
- Gather device information
- Capture photos using the front and back cameras
- Collect contacts and decode messages from IM accounts, including Facebook Messenger, WhatsApp, Skype, Viber, Line, WeChat, Hangouts, Telegram, and BlackBerry Messenger.
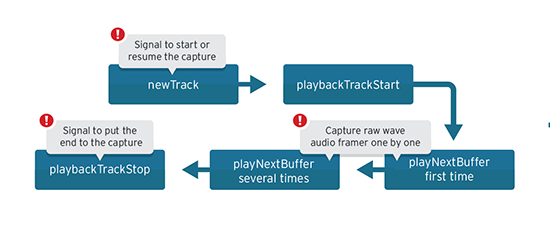
- Capture real-time voice calls in any network or app by hooking into the “mediaserver” system service
RCSAndroid has been actively used since 2012 and has been known to researchers since 2014, when research group Citizen Lab detailed a Hacking Team backdoor used against Android users in Saudi Arabia. According to Trend Micro, the malware used at least two different methods to infect targeted handsets. The first involved text messages that lured users to booby-trapped websites. The malicious sites, in turn, exploited known exploits, designated as CVE-2012-2825 and CVE-2012-2871, and are present in the default browsers found in Android versions from 4.0 to 4.3. A second infection method was to use a fake news app called "BeNews," which as Ars reported earlier this week was available on the official Google Play Android market. E-mails sent among Hacking Team executives showed that engineers were developing updates designed to work on version 5.0, but so far there's no indication any of the source code has gone public.
The Android surveillance suite works like a "cluster bomb" that combines multiple attack tools, including the two exploits described above, low-level coding that greatly expands the type of data attackers can gather from infected phones, a higher-level APK installer package, and a command-and-control server infrastructure infected devices can connect to. Once a phone is infected, it may need its firmware to be reflashed to have the backdoor removed. Android users who want to protect themselves against it should follow the standard security guidance, including avoiding apps installed by third-party services and updating Android devices to the latest available version.
"The leaked RCSAndroid code is a commercial weapon now in the wild," Trend Micro researchers wrote. "Mobile users are called on to be on top of this news and be on guard for signs of monitoring. Some indicators may come in the form of peculiar behavior such as unexpected rebooting, finding unfamiliar apps installed, or instant messaging apps suddenly freezing."
Post updated throughout to correct company name.
reader comments
103