Security researchers have tracked a malware distribution campaign spreading the FinFisher spyware — also known as FinSpy — to the infrastructure of Internet Service Providers (ISPs) in at least two countries.
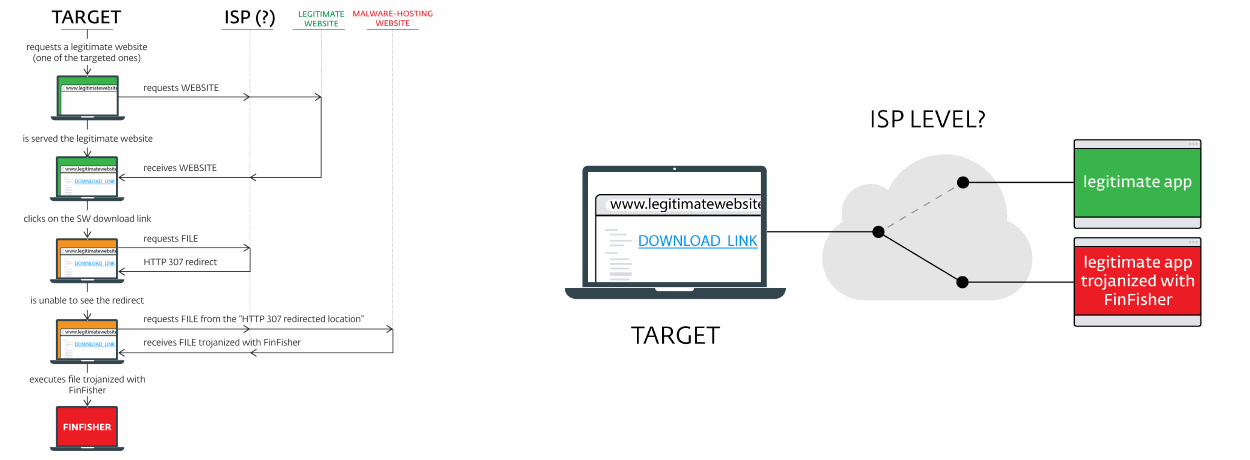
Researchers suspect that ISPs used their ability to control user trafic and redirect users attempting to download certain software to a different link offering the same software, but laced with the FinFisher spyware.
The list of malware-infected applications delivered this way includes products such as WhatsApp, Skype, Avast, WinRAR, VLC Player and others.
ESET, the cyber-security company that detected these download link switcheroos — says it cannot name the countries where it identified the ISP-level intervention "so as not to put anyone in danger."
Attacks most certainly carried out at ISP level
These types of attacks, when a third-party intervenes in a victim's web traffic and switches content, are called Man-in-the-Middle (MitM) attacks.
Researchers say they reached the conclusion that ISPs were carrying out the MitM attacks because recent detections with FinFisher spyware in the two affected countries were spread over a wide geographical area and users could have not been the victims of a MitM attack carried out via local networks, such as WiFi hotspots.
The only technically feasible way to alter the download links for so many apps and so many users across a broad geographical area, in the same way, was with the help of an ISP-level MitM.
Furthermore, documents leaked by WikiLeaks show that the company that sells the FinFisher spyware also provides a package that can be installed at the ISP level.
This package uses temporary HTTP (code 307) redirects. These are the same tyes of redirects ESET saw when ISPs switched the download links with ones for infected apps.
In addition, victims in the two countries used the same Internet provider. It is unclear if the ISPs collaborated willingly, or this was the work of an insider.
Other FinFisher distribution campaigns detected
FinFisher is a powerful surveillance software package sold by Gamma Group, a provider of surveillance tech for law enforcement and government agencies. Experts consider FinFisher malware because it has the same features they often find in spyware strains, such as the ability to record conversations, take screenshots, record videos, steal files, etc..
Besides aiding law enforcement in investigations, there is evidence that FinFisher has been sold to oppressive regimes, which later used it to go after political dissidents, journalists, and other government critics.
FinFisher has been distributed historically just like regular malware, using zero-day exploits, spear-phishing emails, drive-by downloads when users navigate to hacked sites, and by manual installations when physical access is provided to a target's device.
ESET claims this was the first time it saw FinFisher delivered at an ISP level. In addition, ESET says that besides the two countries where the spyware was delivered via ISP-level MitM attacks, it also detected FinFisher distribution campaigns using the classic methods in five other countries.
Earlier this month, FireEye also reported a spear-phishing campaign that spread the FinFisher malware using the Office CVE-2017-8759 vulnerability, a zero-day at the time of its discovery. These attacks targeted Russian-speaking users.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now